-
2 years ago
SplunkNinja wrote a new post
Dashboard: Splunk Insights – Users & Roles
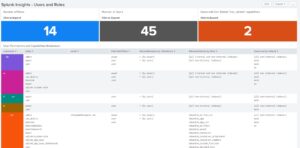 Quick glance into who’s who in the zoo for users, capabilities, roles, and what indexes are searchable. Also calls out users with can_delete […]
Quick glance into who’s who in the zoo for users, capabilities, roles, and what indexes are searchable. Also calls out users with can_delete […] -
2 years, 2 months ago
SplunkNinja wrote a new post
Splunk License Consumption via _introspectionJust sharing a query I found useful lately when licensing dashboards are being silly. Mileage may […]
-
5 years, 4 months ago
SplunkNinja commented on the post, Weekend User Activity
In reply to: SplunkNinja wrote a new post Run the following (modify user field as needed) to show weekend activity:sourcetype="WinEventLog:Security" (date_wday=saturday OR date_wday=sunday) | stats count by Account_Name, date_wdayViewFeel free to join our discord for a live chat & discussion as well as requests! https://discord.gg/K8CFbB7
-
5 years, 4 months ago
SplunkNinja commented on the post, Weekend User Activity
In reply to: SplunkNinja wrote a new post Run the following (modify user field as needed) to show weekend activity:sourcetype="WinEventLog:Security" (date_wday=saturday OR date_wday=sunday) | stats count by Account_Name, date_wdayViewsourcetype=”WinEventLog:Security” (date_wday=saturday OR date_wday=sunday) Account_Name=”user_name_here” | stats count by Account_Name, date_wday
-
5 years, 4 months ago
SplunkNinja wrote a new post
The following simple Splunk query will put all Splunk User accounts with an email address into a panel for copy and paste purposes (such as copying all email addresses to send in an email). I’ve added a semi colon […]
-
5 years, 10 months ago
SplunkNinja commented on the post, Windows Dashboard showing Who (was) logged on to ?
In reply to: DaveyBoy wrote a new post Dashboard with 3 separate columns which allow you to drill into 3 separate assets to find out who was logged on, when they logged on, and how they logged on. Accounts for remote logins, […] ViewArmando,
You’ll need to have access to the correct indexes for this, you might need to manually enter the index name if your role doesn’t search all non-internal indexes by default. -
5 years, 11 months ago
SplunkNinja wrote a new post
Here’s an incredibly simple Splunk query to count the number of characters in an event:
index=* | eval CharCount=len(_raw) -
5 years, 11 months ago
SplunkNinja wrote a new post
Dashboard for Splunk Infrastructure/Server Specs at a Glance
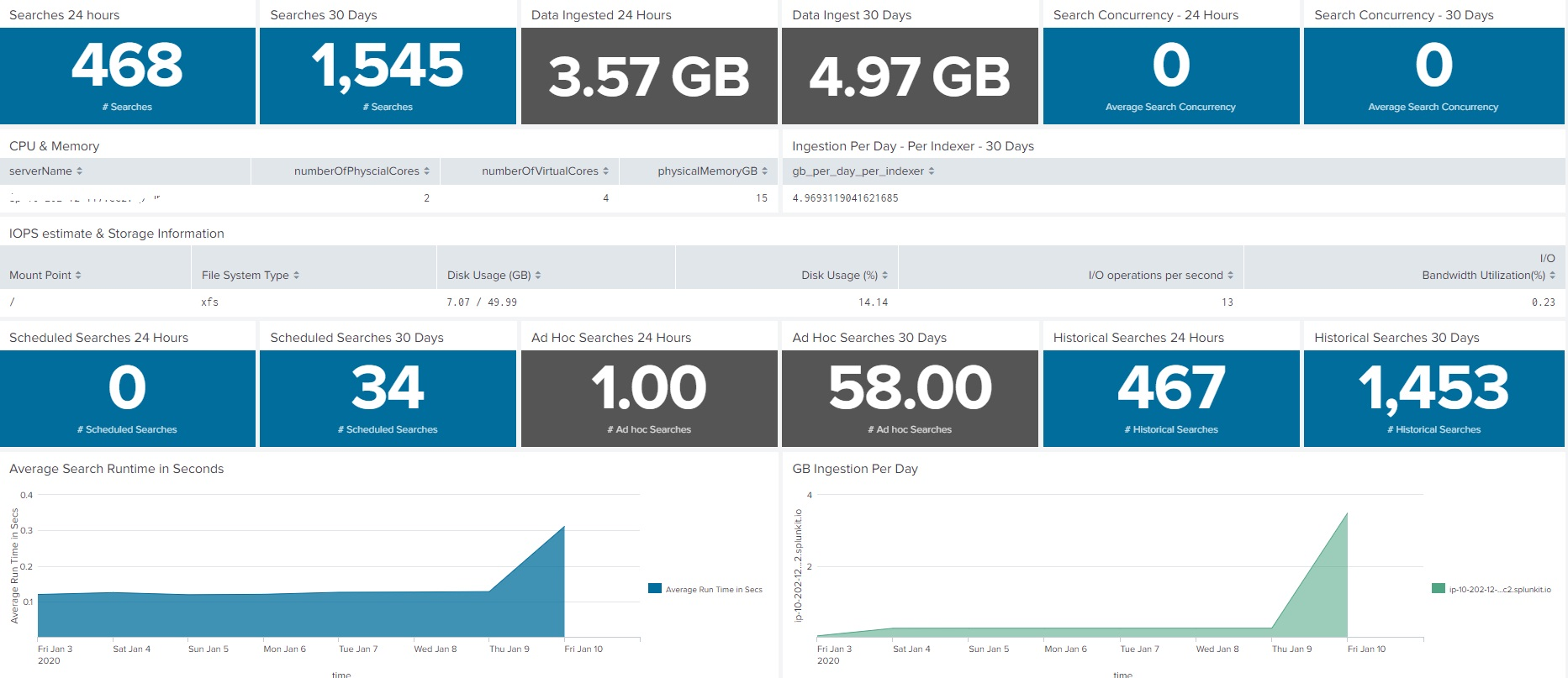 This dashboard will show the server or infrastructure specs of your Splunk environment. This is not […]
This dashboard will show the server or infrastructure specs of your Splunk environment. This is not […] -
6 years, 3 months ago
SplunkNinja commented on the post, Failed Attempts to Logon to Splunk Web
In reply to: SplunkNinja wrote a new post The following Splunk Search Query will return all users who have failed to logon to the Splunk Web console. This query will also include an average (from […] ViewIt’s been….~6 months. I’m going to assume I updated the original here :)
-
6 years, 4 months ago
SplunkNinja commented on the post, Apache Traffic Dashboard
In reply to: SplunkNinja wrote a new post Description: The following Dashboard is what I use to monitor traffic to GoSplunk. It uses the built in sourcetype of access_combined. No additional add-on’s or TA’s are required. I […] ViewJay,
I placed the index=* in there as it will work for any named index. In practice you’ll want to put the name of your index in there. For example: index=”web” -
6 years, 5 months ago
SplunkNinja commented on the post, Successful Login to OSX
In reply to: ItsJohnLocke wrote a new post The following splunk query (with regex) will return a result of users who have successfully authenticated to an OSX machine: *NOTE* Thanks Bob for pointing this out. The regular […] ViewThanks Bob! It has been fixed :)
-
6 years, 5 months ago
SplunkNinja commented on the post, High Level Windows Dashboard
In reply to: SplunkNinja wrote a new post Part 1 – User Logon Activity The following Splunk Dashboard provides a high level view of windows user logon activity. It should be emphasized that the focus of this dashboard […] ViewHopefully soon :)
-
6 years, 5 months ago
SplunkNinja wrote a new post
Want to show what apps have been deployed to forwarders from a deployment server (DS)? Try this Splunk Search:
index=_internal sourcetype=splunkd component=DeployedApplication installing
| stats count […] -
6 years, 5 months ago
SplunkNinja wrote a new post
Need a list of Forwarders that are talking to a Deployment Server? Try this:
index=_internal sourcetype=splunkd component=DC* Handshake | stats count by host
Additional REST query (performed on the DS) will […] -
6 years, 6 months ago
SplunkNinja wrote a new post
Ever want more detailed information on authentications to your WordPress Admin Area? This Splunk Query will show detailed information on successful authentications to the wp-admin section of your […]
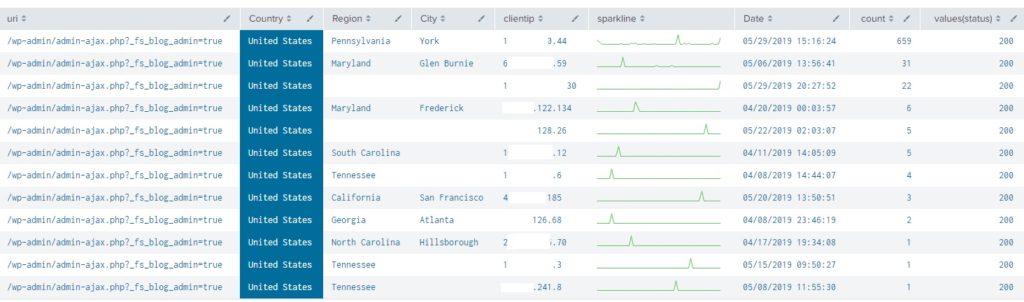
-
6 years, 6 months ago
SplunkNinja commented on the post, License Usage by Index per Day
In reply to: SplunkNinja wrote a new post The following Splunk search query will output license usage for each index for each day for the week to date. It will also output an average for each index over the course of the given […] ViewSpeed Racer,
Good catch. I think an earlier version of this did have an average but was removed for some reason.You’d want to use something like this below but alter it as needed:
index=_internal source=*license_usage.log type=”Usage” splunk_server=*
| eval Date=strftime(_time, “%Y/%m/%d”)
| streamstats sum(b) as volume
| eval…[Read more] -
6 years, 7 months ago
SplunkNinja commented on the post, High Level Windows Dashboard
In reply to: SplunkNinja wrote a new post Part 1 – User Logon Activity The following Splunk Dashboard provides a high level view of windows user logon activity. It should be emphasized that the focus of this dashboard […] ViewThe only thing you’ll need to change is the index= section. Currently it says index=windows_events, change that to the index name where your windows data lives. If you don’t know you can do index=* but that is not best practice.
-
6 years, 7 months ago
SplunkNinja commented on the post, Accounts Deleted within 24 Hours of Creation
In reply to: SplunkNinja wrote a new post This splunk query unmodified will return results on any account regardless of duration, however it uses an “eval case” argument to determine what is “critical” (such as accounts deleted […] ViewDinesh,
Thanks for commenting! Please join our live discussion over in Discord: https://discord.gg/fFJhGPwI’d be happy to expand this query upon successful testing!
-
6 years, 7 months ago
SplunkNinja commented on the post, Auditd hosts in all environments
In reply to: manderso wrote a new post Shows the login activity to our linux environments, sudo commands per host and users. Admin Notes: index=main was changed to index=* due to not everyone using the same index. This […] Viewgbr,
I’m testing the xml and have no issues. Feel free to join our discord and let us know your issue! https://discord.gg/fFJhGPw -
6 years, 8 months ago
SplunkNinja wrote a new post
The following Splunk search extracts the WordPress version from your Apache Web Logs. For fun I also did a time chart using 100% stacked bar chart to show by month each version of wordpress used. This was actually […]
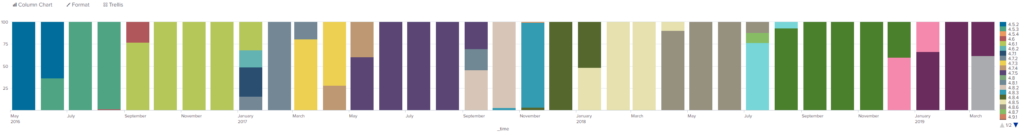
- Load More
