(in reflected attacks a lotof external benign src’s send a lotof packets toward our servers, because our server’s IP spoofed before in request packets and were sent by attacker toward trusted servers and those trusted servers replied us instead of attacker ! ) index=firewall dest=(your company IP range, for example: 184.192.0.0/16) (transport=”udp” AND src_port IN(123,1900,0,53,5353,27015,19,20800,161,389,111,137,27005,520,6881,751,11211,1434,27960,17) AND […]
1st time connection between servers (FTD CISCO)
Description: This query helps you to see all new connections between servers. Still work in progress and can be extended further. “White-listing” happens through the lookup files. Query: index=nfw “Allow” | rex (?:SrcIP.*\b(?<SrcIP>\d+\.\d+\.\d+\.\d+).*DstIP.*\b(?<DstIP>\d+\.\d+\.\d+\.\d+)) | stats count min(_time) AS earliest max(_time) AS maxtime BY SrcIP, DstIP | where earliest>relative_time(now(), “-1d@d”) AND count<=1 | search DstIP=10.0.0.0/8 AND […]
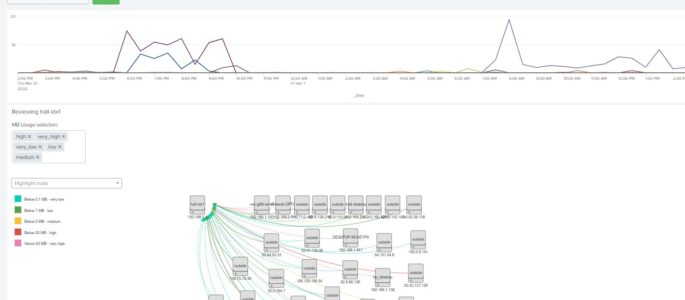
Netflow Activity dashboard showing MB’s in to dest_ip
Description: Dashboard that helps me understand activity in my home lab looking at netflow data from my OPNsense firewall. This dashboard starts with a simple timechart that gives me a trend of average mb_in across all of my devices. I have OPNsense configured to send netflow data v9 to a Splunk independent stream forward which […]
F5 SL ASM iRule Parser for Hosted Deployments
sourcetype=f5:silverline:asm irule=* vs_ip=* | rex “(?<log>.*)” | eval log_stripped = replace(log, “\\\\”,””) | rex field=log_stripped “data=\”(?<data_section>.*?)\”, irule=” | spath input=data_section
Groundspeed Violation/Improbable Access
Oftentimes we are required to determine impossible or improbably access events. Typically, this is a relatively simple thing to do in a modern SIEM, however Splunk, without ESS, does not have a “great” way to handle this type of temporal correlation aside from appends or joins back to the original data. I constructed the following […]
Investigate by MAC, IP all VPN authentications through CISCO_ISE
Helps to investigate authentications through CISCO_ISE device. This identifies who logs in, the MAC address and IP for any use cases index=<your cisco index> “<your IP>” |rex field=”cisco_av_pair” “mdm-tlv=device-mac=(?<MAC_ID>\w+-\w+-\w+-\w+-\w+-\w+)” |rex field=”cisco_av_pair” “mdm-tlv=device-platform=(?<OS>\w+)” |rex field=_raw “(?<IP><IP regex>)” |iplocation IP |stats c sum(Acct_Input_Packets) as Packets_In sum(Acct_Output_Packets) as Packets_Out by _time User_Name Framed_Protocol src_mac City Country Region IP […]
Investigate an IP through Palo Alto Logs
index= <your palo alto index> <IP you want to investigate> |stats c sum(bytes) as Bytes_Out by _time user application action dest_ip dest_location src_ip client_ip client_location session_end_reason “app:able_to_transfer_file” “app:has_known_vulnerability” “app:prone_to_misuse” “app:used_by_malware” “app:evasive” |fields + _time user application action dest_ip dest_location client_ip client_location Bytes_Out session_end_reason “app:able_to_transfer_file” “app:has_known_vulnerability” “app:prone_to_misuse” “app:used_by_malware” “app:evasive” |rename client_ip as SourceIP |fields – user […]
Search All Traffic by src / action – Creates Table
This is a magical query for tracking down all internal resources connecting to or from external IPs and Countries src!=10.0.0.0/8 AND src!=192.168.0.0/12 AND src!=192.168.0.0/16 action=”allowed” | iplocation src | search Country=* | table Country, src, action, bytes_out, packets_out | dedup src | sort Country
Blocked Firewall Scanning Activity with indicator if Source has been allowed.
This search is still a work in progress, but thought I would go ahead and post it. Currently use OPNsense firewall in my house. The purpose of the search is to identify blocked scanning activity on my firewall that does a 2nd search via a join to add if any src_ip that had been blocked […]