index=_audit action=edit* info=granted operation!=list host= object=* | transaction action user operation host maxspan=30s | stats values(action) as action values(object) as modified_object by _time,operation,user,host | rename user as modified_by | table _time action modified_object modified_by
Splunk dashboard that displays User searches
Built this dashboard to give a high level overview of user search activity. The search powering the dashboard is looking that the _audit index and you will need to ensure that you have proper access to the internal Splunk indexes. The dashboard includes a TimeRange picker, radio button to include or exclude Splunk’s system user, […]
Triggered Alert Analytics
Primary Dashboards Contains alert analytics for both triggered alerts and saved searches. Please replace $name$ with the saved search naming convention you utilize (ie. 0001 – AlertName). You will need an outputlookup to generate the bottom two tables; it will be based on the query that generates the second table in the dashboard. <form theme=”dark”> […]
Show your triggered alerts
This search shows all the alerts that where triggered in your splunk environment: index=_audit action=alert_fired ss_app=* | eval ttl=expiration-now() | search ttl>0 | convert ctime(trigger_time) | table trigger_time ss_name severity | rename trigger_time as “Alert Time” ss_name as “Alert Name” severity as “Severity”
Find unused dashboards
Use this search to find unused dashboards: | rest /servicesNS/-/-/data/ui/views splunk_server=* | search isDashboard=1 | rename eai:acl.app as app | fields title app | join type=left title [| search index=_internal sourcetype=splunk_web_access host=* user=* | rex field=uri_path “.*/(?<title>[^/]*)$” | stats latest(_time) as Time latest(user) as user by title ] | where isnotnull(Time) | eval Now=now() | […]
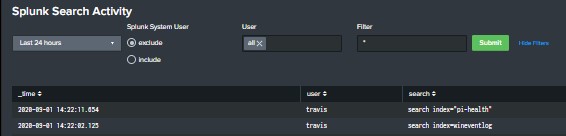
Show Searches with Details (Who | When | What)
The following Splunk search will show a list of searches ran on a splunk server with the following details: Who ran the search What sourcetype was used What index was used What the search string was When the search was last ran index=_audit action=search sourcetype=audittrail search_id=* NOT (user=splunk-system-user) search!=”‘typeahead*” | rex “search\=\'(search|\s+)\s(?P<search>[\n\S\s]+?(?=\’))” | rex field=search […]