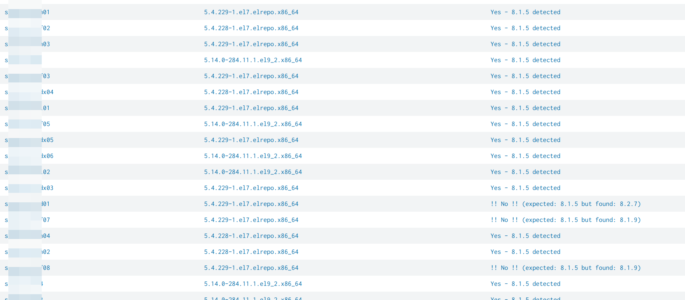
simply query to compare an expected splunk version with reality. simply adjust “expected_version” to your expected version: | rest splunk_server=* /services/server/status/resource-usage/hostwide | table splunk_server splunk_version| eval expected_version=”8.1.5″| eval match_expectation=if(splunk_version == expected_version, “Yes – ” . expected_version . ” detected”, “!! No !! (expected: ” . expected_version . ” but found: ” . splunk_version . “)”)| […]
Show all successful splunk configuration changes by user
index=_audit action=edit* info=granted operation!=list host= object=* | transaction action user operation host maxspan=30s | stats values(action) as action values(object) as modified_object by _time,operation,user,host | rename user as modified_by | table _time action modified_object modified_by
skipped searches and why
Quickly identify high amounts of skipped searches in your cluster or standalone SH(s): index = _internal skipped sourcetype=scheduler status=skipped host=[your splunk SH(s)] | stats count by app search_type reason savedsearch_name | sort -count Adjust “[your splunk SH(s)]” to the SH(s) you want to check obviously ;)
find blocking queues
Blocked queues are (obviously) bad for your environment so here a search to identify those: index=_internal sourcetype=splunkd group=queue (name=parsingQueue OR name=indexqueue OR name=tcpin_queue OR name=aggqueue) | eval is_blocked=if(blocked==”true”,1,0), host_queue=host.” – “.name | stats sparkline sum(is_blocked) as blocked,count by host_queue | eval blocked_ratio=round(blocked/count*100,2) | sort 20 -blocked_ratio | eval requires_attention=case(blocked_ratio>50.0,”fix highly recommended!”,blocked_ratio>40.0,”you better check..”,blocked_ratio>20.0,”usually no need […]
identify knowledge objects, permissions and extractions
The following will: list all knowledge objects for your SH (or given search peer(s)) each objects name, type, app, permissions, sharing (e.g. global, app, private) and owner if props-extract: the props stanza, props type (e.g if its Inline or Transforms), props sourcetype and props value (e.g. the regex) if transforms-extract: the state (tf_disabled), format (tf_format), tf_fields […]
List permissions for Users, roles, allowed indexes and indexes searched by default
Ok that one is a big one so be prepared ;) The following will (on a SH / SH Cluster): list all users and their roles list inherited roles list all indexes allowed by the shown roles list all indexes allowed for inherited roles (one level!) inherited allowed indexes will show the originator (which inherited […]
count all events for 1 or multiple index(es)
Total count of all events for 1 or more index(es) Approach 1 (fastest) | eventcount index=foo or | eventcount index=foo index=bar does *not* support time ranges in the time picker tested on: splunk v6.6 Approach 2 (fast – especially when tsidx are *not* reduced) | tstats count where index=foo OR index=bar by span=1d _time index […]