(updated on 8/26/2020)
Working with a customer I started this dashboard to give a high level overview of Windows Sysmon data. I have been evolving the dashboard in my home environment and will take any feedback to improve the effectiveness of this dashboard.
First is getting sysmon data into your splunk environment. My home computers are running Windows 10 home edition (i know, need to upgrade to pro) and needed to install/configure sysmon.
I first downloaded sysmon from the Microsoft sysinternals suite: https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
Next I installed the Splunk Add-on for Microsoft Sysmon: https://splunkbase.splunk.com/app/1914/
Found the following presentation from Splunk .conf2017 that covered using SwiftOnSecurity’s config as a baseline and how the presenter modified it to meet their needs: https://conf.splunk.com/files/2017/slides/effectively-enhancing-our-soc-with-sysmon-powershell-logging-and-machine-learning-to-detect-and-respond-to-todays-threats.pdf
Here is SwiftOnSecurity’s GitHub site that includes a Sysmon configuration file for everybody to fork and tutorial/guide for Sysmon setup: https://github.com/SwiftOnSecurity/sysmon-config
Also here is another presentation around sysmon, SwiftOnSecurity and even filter examples: https://sector.ca/wp-content/uploads/presentations18/Morin_Sysmon_2019-16-9.pdf
Just released from Malware Archaeology is this “Windows Sysmon Logging Cheat Sheet” that is intended to help you understand where Microsoft’s FREE Sysinternals Sysmon agent can supplement and enhance your Windows Logging, NOT replace it. https://www.malwarearchaeology.com/s/Windows-Sysmon-Logging-Cheat-Sheet_Aug_2019-pthx.pdf
With sysmon configuration completed next I pushed an updated inputs.conf to all of my windows machines. Example of the inputs.conf sysmon entry:
[WinEventLog://Microsoft-Windows-Sysmon/Operational] disabled = 0 renderXml = 1 index = sysmon source = XmlWinEventLog:Microsoft-Windows-Sysmon/Operational
The queries in the dashboard are using index=sysmon since that is where I store my sysmon data, adjust as needed.
I have also built a lookup table called process_path.csv to filter out validated process_paths which is enable or disable by radio buttons at the top of the dashboard. My suggestion would be to build you own process_path.csv file either by the outputlookup command then validate the output or manually create the csv. Another helpful app for editing lookup files that I have installed is Lookup File Editor app:https://splunkbase.splunk.com/app/1724/
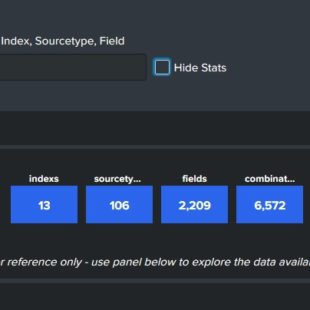
The 2nd panel includes a dynamic field selection input that will show you all the fields available which includes using an eval to populate a “time” field and iplocation to give you more information on destination IP’s when available.
<form theme="dark" version="1.0">
<label>Win Sysmon Process View</label>
<description>Dashboard is built to review windows sysmon processes that are running.</description>
<fieldset submitButton="true" autoRun="false">
<input type="time" token="time1" searchWhenChanged="false">
<label></label>
<default>
<earliest>-24h@h</earliest>
<latest>now</latest>
</default>
</input>
<input type="radio" token="filter2">
<label>Click to filter know processes</label>
<choice value="*">All processes</choice>
<choice value="NOT [| inputlookup process_path.csv]">Exclude know processes</choice>
<default>*</default>
<initialValue>*</initialValue>
</input>
<input type="text" token="filter1">
<label>Filter the dashboard</label>
<default>*</default>
</input>
</fieldset>
<row>
<panel>
<title>Filtering events = $filter1$ & $filter2$</title>
<table>
<search>
<query>index=sysmon source="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" $filter1$ $filter2$ * NOT [| inputlookup process_path.csv] | stats count by process_path process_exec | eval path_bar="(".count.") "+process_path | stats values(path_bar) as Process_Path dc(process_path) as Number_Different_Paths sum(count) as Total by process_exec | sort -Total</query>
<earliest>$time1.earliest$</earliest>
<latest>$time1.latest$</latest>
<sampleRatio>1</sampleRatio>
</search>
<option name="count">20</option>
<option name="dataOverlayMode">none</option>
<option name="drilldown">cell</option>
<option name="percentagesRow">false</option>
<option name="refresh.display">progressbar</option>
<option name="rowNumbers">false</option>
<option name="totalsRow">false</option>
<option name="wrap">true</option>
<drilldown>
<set token="exe">$click.value$</set>
</drilldown>
</table>
</panel>
</row>
<row>
<panel>
<title>Looking at $exe$</title>
<input type="multiselect" token="field2" searchWhenChanged="true">
<label>Field Selection:</label>
<default>time,host,ParentCommandLine</default>
<delimiter> </delimiter>
<fieldForLabel>field</fieldForLabel>
<fieldForValue>field</fieldForValue>
<search>
<query>index=sysmon source="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" $filter1$ $filter3$ process_exec="$exe$" | eval time=strftime(_time, "%Y-%m-%d %H:%M:%S") | iplocation prefix=Dest_ dest_ip | fillnull value=NULL $field2$ | fieldsummary
| where count>0</query>
<earliest>$time1.earliest$</earliest>
<latest>$time1.latest$</latest>
</search>
<initialValue>time,host,ParentCommandLine</initialValue>
</input>
<input type="text" token="filter3" searchWhenChanged="true">
<label>Filter this panel:</label>
<default>*</default>
<initialValue>*</initialValue>
</input>
<table>
<search>
<query>index=sysmon source="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" $filter1$ $filter3$ process_exec="$exe$" | eval time=strftime(_time, "%Y-%m-%d %H:%M:%S") | iplocation prefix=Dest_ dest_ip | fillnull value=NULL $field2$ | stats count by $field2$ | sort -count</query>
<earliest>$time1.earliest$</earliest>
<latest>$time1.latest$</latest>
</search>
<option name="count">10</option>
<option name="drilldown">row</option>
<option name="refresh.display">progressbar</option>
<drilldown>
<link target="_blank">search?q=index%3Dsysmon%20source%3D%22XmlWinEventLog%3AMicrosoft-Windows-Sysmon%2FOperational%22%20$filter1$%20$filter3$%20process_exec%3D%22$exe$%22%20%7C%20fillnull%20value%3DNULL%20$field2$%20%7C%20stats%20count%20by%20$field2$%20%7C%20sort%20-count&earliest=$time1.earliest$&latest=$time1.latest$</link>
</drilldown>
</table>
</panel>
</row>
</form>