This relies on the search posted earlier: This will display storage and license usage broken down by groups, predefined in the chargeback app customers.csv <form> <label>License and Storage Usage</label> <fieldset submitButton=”false”> <input type=”dropdown” token=”grouppicker”> <label>Group</label> <choice value=”Group1″>Group1</choice> <choice value=”Group2″>Group2</choice> <choice value=”Group3″>Group3</choice> <choice value=”Group4″>Group4</choice> <choice value=”Group5″>Group5</choice> <choice value=”Group6″>Group6</choice> <choice value=”*”>All Groups</choice> <default>*</default> </input> </fieldset> <row> <panel> […]
Build License usage by Group
This was cobbled together from multiple searches I found. This search feeds the license and storage dashboard posted here: It relies on the Chargeback app for the customers.csv form. index=_internal source=*license_usage.log type=”Usage” earliest=-30d@d latest=@d | eval indexname = if(len(idx)=0 OR isnull(idx),”(UNKNOWN)”,idx) | eval sourcetypename = st | bin _time span=1d | stats values(poolsz) as poolsz […]
Detailed User Activity
index=_* search=* user=* user!=- user!=splunk-system-user | rex field=search max_match=0 “index\s*=[\s\”]*(?<idx1>.*?)[\|\s\”\)]” | rex field=search max_match=0 “[\+\(|\+]index\%3D(?<idx2>.*?)[\+|\)\+]” | eval idx=if(isnull(idx1), idx2, idx1) | eval frequency=if(source=”/opt/splunk/var/log/splunk/splunkd_access.log”, “scheduled”, “ad-hoc”) | eval type=if(match(search, “summary*”), “summary”, type1) | eval idx=if(isnull(idx), “NONE”, idx) | eval end_type=if(frequency=”ad-hoc”, “ad-hoc”, type) | rename end_type as type | table _time frequency type source user idx search […]
Exclude single event type from logs
Do this on HF transforms.conf: [discard_gotoips] REGEX = <<<use regex,URL>>> DEST_KEY = queue FORMAT = nullQueue props.conf: [default] TRANSFORMS-null = discard_gotoips File location: /etc/system/local
Who’s Using Splunk?
I often get asked how much a certain dashboard gets looked at, or how many times a user looks at a specific app. I wrote this quick query to answer that question. index=_internal sourcetype=”splunk_web_access” method=”GET” status=”200″ | stats count as count by user, view | appendpipe [stats sum(count) as count by user | eval view […]
Find unused dashboards
Use this search to find unused dashboards: | rest /servicesNS/-/-/data/ui/views splunk_server=* | search isDashboard=1 | rename eai:acl.app as app | fields title app | join type=left title [| search index=_internal sourcetype=splunk_web_access host=* user=* | rex field=uri_path “.*/(?<title>[^/]*)$” | stats latest(_time) as Time latest(user) as user by title ] | where isnotnull(Time) | eval Now=now() | […]
skipped searches and why
Quickly identify high amounts of skipped searches in your cluster or standalone SH(s): index = _internal skipped sourcetype=scheduler status=skipped host=[your splunk SH(s)] | stats count by app search_type reason savedsearch_name | sort -count Adjust “[your splunk SH(s)]” to the SH(s) you want to check obviously ;)
find blocking queues
Blocked queues are (obviously) bad for your environment so here a search to identify those: index=_internal sourcetype=splunkd group=queue (name=parsingQueue OR name=indexqueue OR name=tcpin_queue OR name=aggqueue) | eval is_blocked=if(blocked==”true”,1,0), host_queue=host.” – “.name | stats sparkline sum(is_blocked) as blocked,count by host_queue | eval blocked_ratio=round(blocked/count*100,2) | sort 20 -blocked_ratio | eval requires_attention=case(blocked_ratio>50.0,”fix highly recommended!”,blocked_ratio>40.0,”you better check..”,blocked_ratio>20.0,”usually no need […]
Regex Extraction for WordPress Version from Apache Logs
The following Splunk search extracts the WordPress version from your Apache Web Logs. For fun I also did a time chart using 100% stacked bar chart to show by month each version of wordpress used. This was actually a pretty neat display of colors to show the upgrade path of WordPress over the years! I […]
Utilizing tstats for Page Views within Apache Web Logs
Here’s a Splunk query to show a timechart of page views from a website running on Apache. Due to the search utilizing tstats, the query will return results incredibly fast over a very LONG period of time if desired. Change the index to reflect yours, as well as the span to reflect a span you […]
Windows RDP sessions
Here is a dashboard I built to look at Windows Logon Type 2 & 10 (remote & remote interactive) that will help identify which users access which servers and how many times. Also when you click on a user it will run a 30 day search and a 24 hour search that produces a column […]
Successful File Access Attempts and Filename Accessed
Ever need to find when a user accessed a file within a Windows environment? The following Splunk query will show successful file accesses by each user for a given day. Depending on the size of your environment this can get out of hand quickly. You’ll want to tweak to best fit your environment. *Note* you […]
Internal Splunk User Stats
This simple Splunk query will show us unique Splunk user logged into Splunk per day, as well as total count of log-ons. index=_audit info=succeeded | timechart span=1d dc(user) as unique_users count(user) as logons_all_users
Apache Traffic Dashboard
Description: The following Dashboard is what I use to monitor traffic to GoSplunk. It uses the built in sourcetype of access_combined. No additional add-on’s or TA’s are required. I replaced my index with index=* so it’ll work out of the box. You’ll want to change this to your index for best practices. *UPDATE – 2019/05/29* […]
Check your strftime is correct in the props.conf
A simple method on checking if your strftime (TIME_FORMAT=) in the props.conf matches your log file timestamp format. strftime(X,Y) This function takes a UNIX time value, X, as the first argument and renders the time as a string using the format specified by Y. The UNIX time must be in seconds. Use the first 10 […]
List all ES Correlation Searches
| rest splunk_server=local count=0 /services/saved/searches | where match(‘action.correlationsearch.enabled’, “1|[Tt]|[Tt][Rr][Uu][Ee]”) | rex field=action.customsearchbuilder.spec “datamodel\\\”:\s+\\\”(?<Data_Model>\w+)” | rex field=action.customsearchbuilder.spec “object\\\”:\s+\\\”(?<Dataset>\w+)” | rename action.correlationsearch.label as Search_Name title as Rule_Name eai:acl.app as Application_Context request.ui_dispatch_app as UI_Dispatch_Context description as Description Data_Model as Guided_Mode:Data_Model Dataset as Guided_Mode:Dataset action.customsearchbuilder.enabled as Guided_Mode action.customsearchbuilder.spec as Guided_Mode:Search_Logic search as Search dispatch.earliest_time as Earliest_Time dispatch.latest_time as Latest_Time […]
Windows service activity & MSI installs
Here is a dashboard I built to help you understand the activity of services and MSI installs within a Windows machine. This dashboard utilizes Post Processing so there is only 2 searches that are launched when the dashboard is loaded to minimize impact on search queuing. Add-on’s: Splunk Add-on for Microsoft Windows – https://splunkbase.splunk.com/app/742/ Video overview […]
Windows Account Management Dashboard
Here is a dashboard that I have built to look at Windows Account Management events. The dashboard utilizes a drill-down that will feed a multi-select which is using a dynamic search to give you fields that are available for the stats output in 2nd panel dependent on your selection. Add-on’s: Splunk Add-on for Microsoft Windows […]
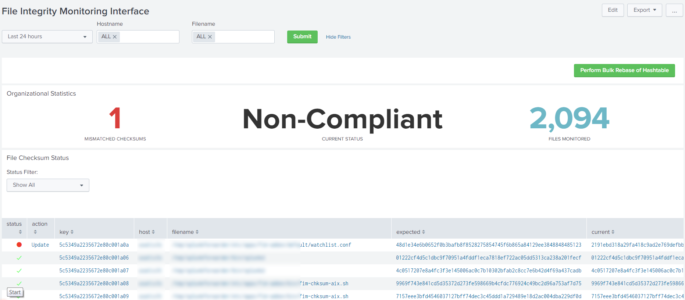
Simple File Integrity Monitoring Management Dashboard
This is the code for my original reddit post at https://www.reddit.com/r/Splunk/comments/am3tgr/simple_file_integrity_monitoring/ This dashboard allows users to manage simple File Integrity Monitoring (FIM) within Splunk. Please note that this isn’t a full FIM suite as it only validates if a checksum has been changed on a file, but I have included a simple TA for Linux. However, if you […]
Auditd hosts in all environments
Shows the login activity to our linux environments, sudo commands per host and users. Admin Notes: index=main was changed to index=* due to not everyone using the same index. This dashboard has been tested for code errors, but not for search errors. Please comment if you have any issues! <form> <label>Audit All Hosts</label> <fieldset submitButton=”false”> […]