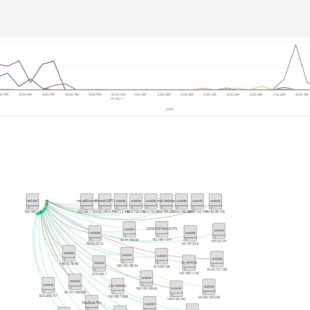
(in reflected attacks a lotof external benign src’s send a lotof packets toward our servers, because our server’s IP spoofed before in request packets and were sent by attacker toward trusted servers and those trusted servers replied us instead of attacker ! )
index=firewall dest=(your company IP range, for example: 184.192.0.0/16) (transport="udp" AND src_port IN(123,1900,0,53,5353,27015,19,20800,161,389,111,137,27005,520,6881,751,11211,1434,27960,17) AND src_port!=dest_port) OR ( (transport="tcp") AND src_port=80 AND dest_port!=80)) |bin _time span=5m |fields src_port,dest,src |stats count,dc(src) as src_count , dc(dest) as dest_count by src_port,_time |eval First_Factor=src_count/dest_count (in reflected attacks this ratio is to high!) |eval Final_Factor=First_Factor+count (the count of replies is another important factor ) |search Final_Factor>1200 |eval msg="Reflected DDoS Attack has been detected. "."count:".count." from ".src_count. " distict sources with same src_port:".src_port." on ". dest_count. " servers" |fields msg