Ever need to find when a user accessed a file within a Windows environment? The following Splunk query will show successful file accesses by each user for a given day. Depending on the size of your environment this can get out of hand quickly. You’ll want to tweak to best fit your environment. *Note* you […]
Windows security daily domain activities
sourcetype=WinEventLog:Security src_nt_domain!=”NT AUTHORITY” EventCode=4720 OR EventCode=4726 OR EventCode=4738 OR EventCode=4767 OR EventCode=4781 OR EventCode=4727 OR EventCode=4730 OR EventCode=4731 OR EventCode=4734 OR EventCode=4735 OR EventCode=4737 OR EventCode=4744 OR EventCode=4745 OR EventCode=4748 OR EventCode=4749 OR EventCode=4750 OR EventCode=4753 OR EventCode=4754 OR EventCode=4755 OR EventCode=4758 OR EventCode=4759 OR EventCode=4760 OR EventCode=4763 OR EventCode=4764 OR EventCode=4728 OR EventCode=4729 OR […]
identify knowledge objects, permissions and extractions
The following will: list all knowledge objects for your SH (or given search peer(s)) each objects name, type, app, permissions, sharing (e.g. global, app, private) and owner if props-extract: the props stanza, props type (e.g if its Inline or Transforms), props sourcetype and props value (e.g. the regex) if transforms-extract: the state (tf_disabled), format (tf_format), tf_fields […]
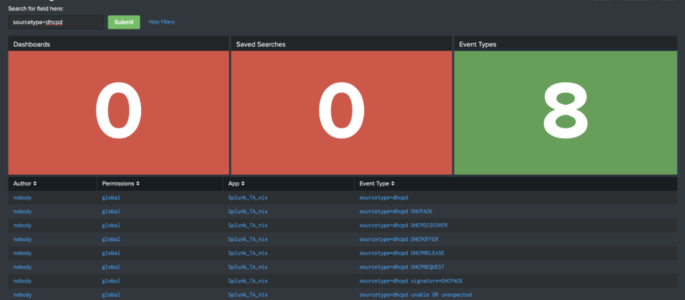
Searching Your Searches
Below is the raw XML of a dashboard we wrote about on our blog a couple of months ago. Click here to read that blog, or copy/paste this XML in your Splunk instance! <form theme=”dark”> <label>Searching for Searches</label> <fieldset submitButton=”true”> <input type=”text” token=”search_input”> <label>Search for field here:</label> </input> </fieldset> <row> <panel> <title>Dashboards</title> <single> <search> <query>| […]
Sysmon – cmd line for non -local connections
sourcetype=”xmlwineventlog:microsoft-windows-sysmon/operational” EventCode=3 Protocol=tcp Initiated=true | where DestinationIp!=”127.0.0.1″ AND DestinationHostname!=SourceHostname| table _time User Computer ProcessId ProcessGuid DestinationHostname DestinationPort | join type=inner [ search sourcetype=”xmlwineventlog:microsoft-windows-sysmon/operational” EventCode=1 | table _time ProcessGuid ProcessId CommandLine]
Weekend User Activity
Run the following (modify user field as needed) to show weekend activity: sourcetype=”WinEventLog:Security” (date_wday=saturday OR date_wday=sunday) | stats count by Account_Name, date_wday
Security Access granted to an Account
Like most windows security logs there are two formats depending on which version of windows you are running. The query for a Windows 7 / Server 2008 and newer looks like this: sourcetype=”WinEventLog:Security” EventCode=4717 | eval Date=strftime(_time, “%Y/%m/%d”) | stats count by src_user, user, Access_Right, Date, Keywords |rename src_user as “Source Account” | rename user […]
System Security Access Removed from Account
The following queries will list security access that was removed from an account in a Windows environment. Queries look different depending on which version of Windows you are running as the syntax and the EventID’s changed after 2003. Windows Server 2008 and newer: sourcetype=”WinEventLog:Security” EventCode=4718 | eval Date=strftime(_time, “%Y/%m/%d”) | stats count by src_user, user, […]
REST API: Table all Splunk User Email Addresses
The following simple Splunk query will put all Splunk User accounts with an email address into a panel for copy and paste purposes (such as copying all email addresses to send in an email). I’ve added a semi colon delimiter in order to literally be copy and paste into an application such as Microsoft Outlook. […]
Search for disabled AD accounts that have been re-enabled
This is a search you can use as an alert or whatever you desire to look for AD accounts that have been disabled in the past 90 days then re-enabled in the past 24h. You can tweak as needed. index=YOURINDEX EventCode IN (4725,4722) earliest=-90d | eval account=mvindex(Account_Name,1) “`separate out the account from the logs and […]
Unable to get a search to work properly
Hi All, I have been trying to get the following search to work for weeks now, with no luck. My entire team has looked at it as well as our local user group and our Account Manager’s SE. No one has been able to figure out why the search isn’t working properly. Here is some […]
Show Searches with Details (Who | When | What)
The following Splunk search will show a list of searches ran on a splunk server with the following details: Who ran the search What sourcetype was used What index was used What the search string was When the search was last ran index=_audit action=search sourcetype=audittrail search_id=* NOT (user=splunk-system-user) search!=”‘typeahead*” | rex “search\=\'(search|\s+)\s(?P<search>[\n\S\s]+?(?=\’))” | rex field=search […]
System Time Modifications in Windows
The following queries will return modifications to time in a windows environment. It ignores system and service accounts. Windows 2008 and newer: source=”WinEventLog:Security” EventCode=4616 (NOT Account_Name=”*$”) (NOT Account_Name=”LOCAL SERVICE”)| eval Date=strftime(_time, “%Y/%m/%d %H:%M:%S”)| eval oldtime = strptime(replace(Previous_Time, “\D”, “”), “%Y%m%d%H%M%S%9N”) | eval t=_time | rename t as “eventtime” |eval diff=round(((eventtime-oldtime)/60)/60,2) | where diff!=0| stats count […]
Windows Time Change
This query will list all users who initiated a time change. System accounts change time automatically, as such I’ve ignored system accounts from the query output. Windows 2008 and newer: sourcetype=WinEventLog:Security EventCode=4616 Account_Name!=”*$” Account_Name!=”LOCAL SERVICE”| stats count by Account_Name Windows 2003 and before: sourcetype=WinEventLog:Security user!=”*$” user!=”LOCAL SERVICE” EventCode=520 | stats count by user
Groundspeed Violation/Improbable Access
Oftentimes we are required to determine impossible or improbably access events. Typically, this is a relatively simple thing to do in a modern SIEM, however Splunk, without ESS, does not have a “great” way to handle this type of temporal correlation aside from appends or joins back to the original data. I constructed the following […]
List All Splunk Users & Associated Roles
The following Splunk query will show a table of all users and their roles: | rest /services/authentication/users | stats values(roles) as Roles by user *Admin Notes* I’ve found the following query to work better in my environment: | rest /services/authentication/users | stats values(roles) as Roles by title
Searches to check search concurrency for historical or real time
The following Splunk search will output historical or real time concurrency in a timechart by host. *NOTE* Change the text <search_head> to your search heads name, alternatively use a *. index=_internal host= source=*metrics.log group=search_concurrency “system total” NOT user=* | timechart max(active_hist_searches) by host index=_internal host= source=*metrics.log group=search_concurrency “system total” NOT user=* | timechart max(active_realtime_searches) by […]
Data model Acceleration Details
This Splunk Search shows you a lot of good information about your data model acceleration and performance. | rest /services/admin/summarization by_tstats=t splunk_server=local count=0 | eval key=replace(title,((“tstats:DM_” . ‘eai:acl.app’) . “_”),””), datamodel=replace(‘summary.id’,((“DM_” . ‘eai:acl.app’) . “_”),””) | join type=left key [| rest /services/data/models splunk_server=local count=0 | table title, “acceleration.cron_schedule”, “eai:digest” | rename title as key | […]
Index Modifications
This Splunk query should show which users attempted to modify an index and if that action was successful: index=_audit user=* action=indexes_edit | stats count by index info user action
Splunk Objects With Permissions Granted to Non-existent Roles
Useful search to show a bit of detail on roles and user permissions. | rest /servicesNS/-/-/admin/directory count=0 splunk_server=local | fields eai:acl.app, eai:acl.owner, eai:acl.perms.*, eai:acl.sharing, eai:location, title | eval perms=mvappend(‘eai:acl.perms.read’,’eai:acl.perms.write’) | fields – eai:acl.perms.* | mvexpand perms | where perms!=”*” AND NOT [ | rest /servicesNS/-/-/authorization/roles count=0 splunk_server=local | fields title | rename title as perms […]