-
2 years, 8 months ago
thall commented on the post, Windows RDP sessions
In reply to: thall wrote a new post Windows RDP sessionsHere is a dashboard I built to look at Windows Logon Type 2 & 10 (remote & remote interactive) that will help identify which users access which servers and […] ViewThanks for bringing this to my attention.
Why you are getting the error is because the “join” command is looking for search that is not there.
There seems to be an issue with the GoSplunk site where part of the 2nd query that is wrapped in square brackets [ ] is not showing up in the post. However, when editing the post the whole query…[Read more]
-
3 years, 4 months ago
thall wrote a new post
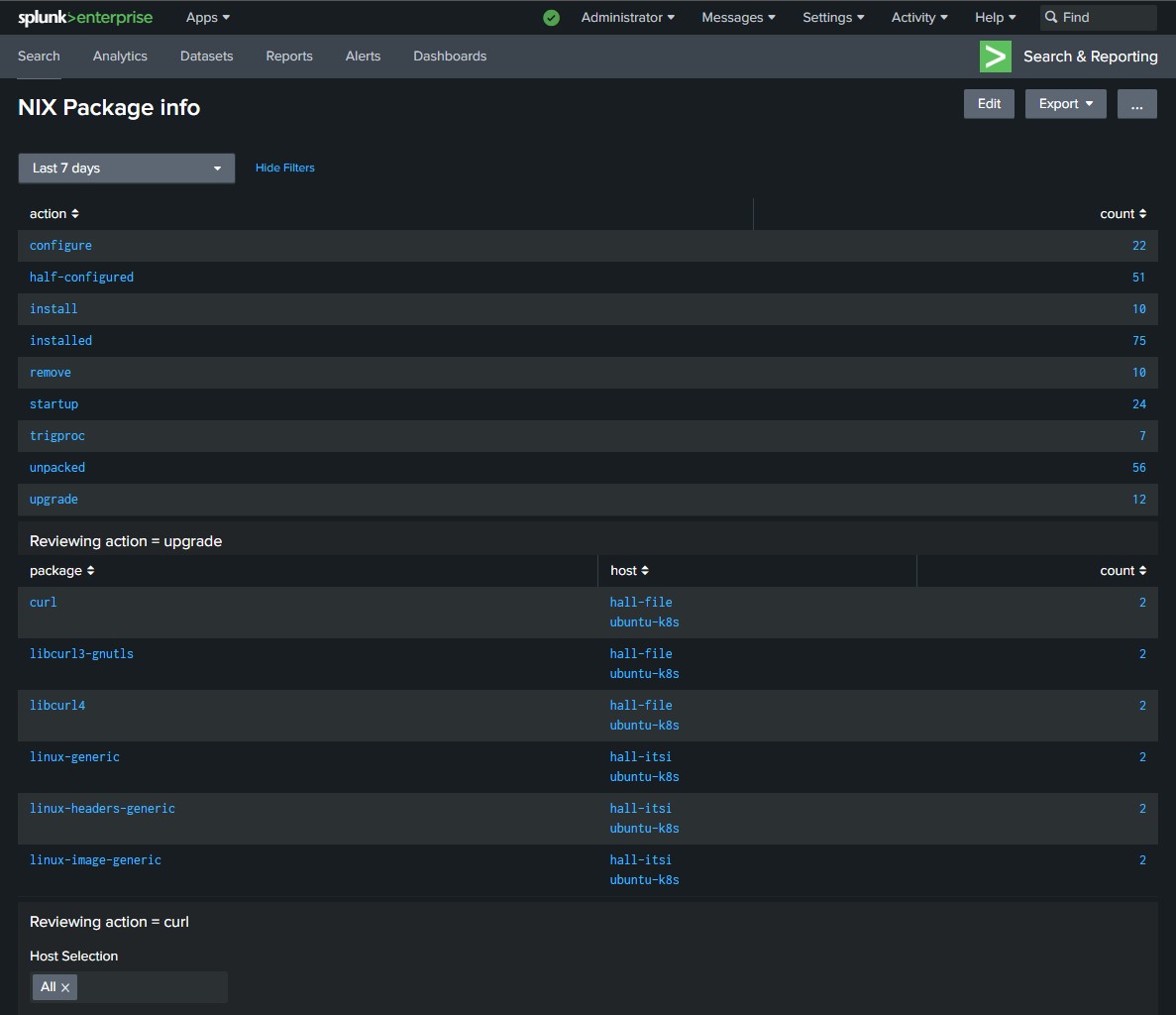
Description:
Wanted a dashboard that would provide information around package information across my Ubuntu servers. At this time I have only built this dashboard to review the “dpkg.log”.
In an attempt to help […]
-
3 years, 9 months ago
thall wrote a new post
Updated Netflow Activity dashboard
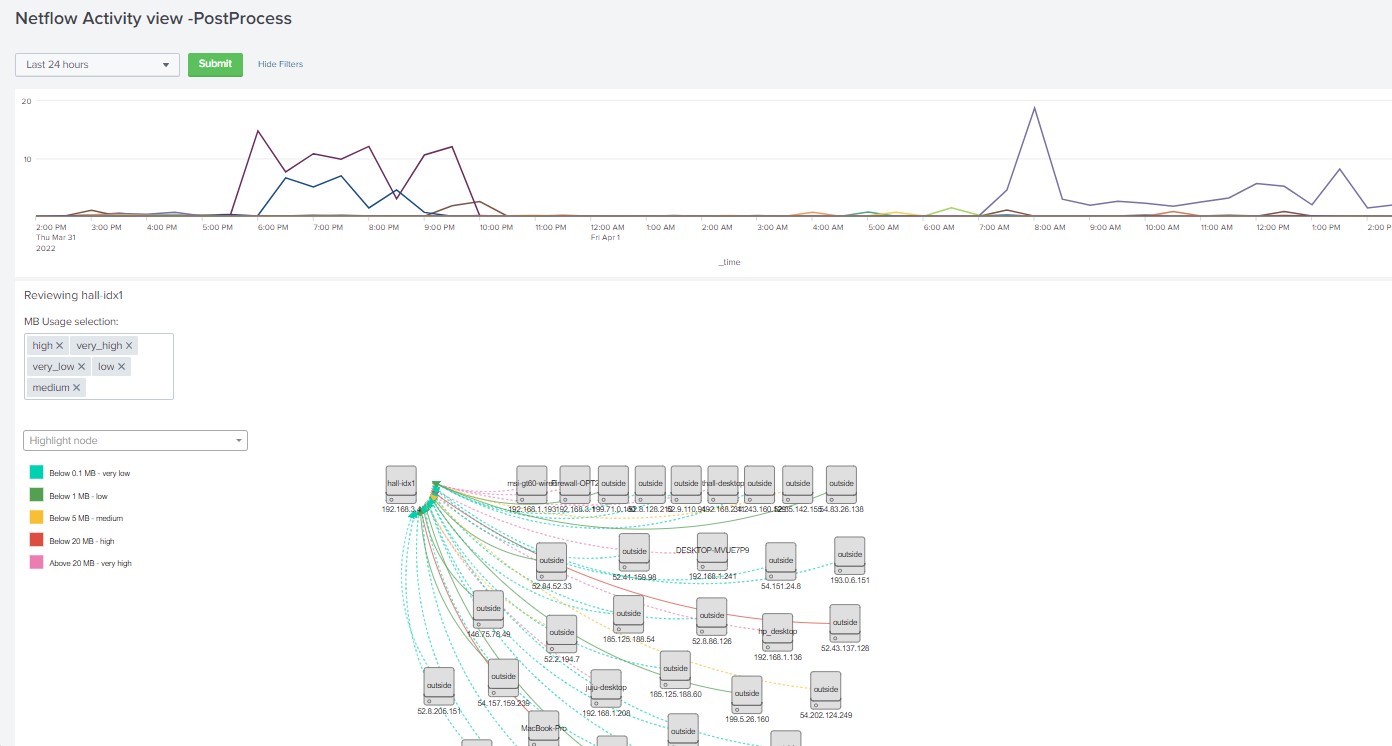 Description: I decided to revisit my Netflow Activity dashboard and make some much-needed improvements. While […]
Description: I decided to revisit my Netflow Activity dashboard and make some much-needed improvements. While […] -
3 years, 11 months ago
thall wrote a new post
Description:
Built this dashboard to display login activity for my *nix host devices. At the top you have a box called “Filter” that allows you to insert search parameters in the base search (ex: user […]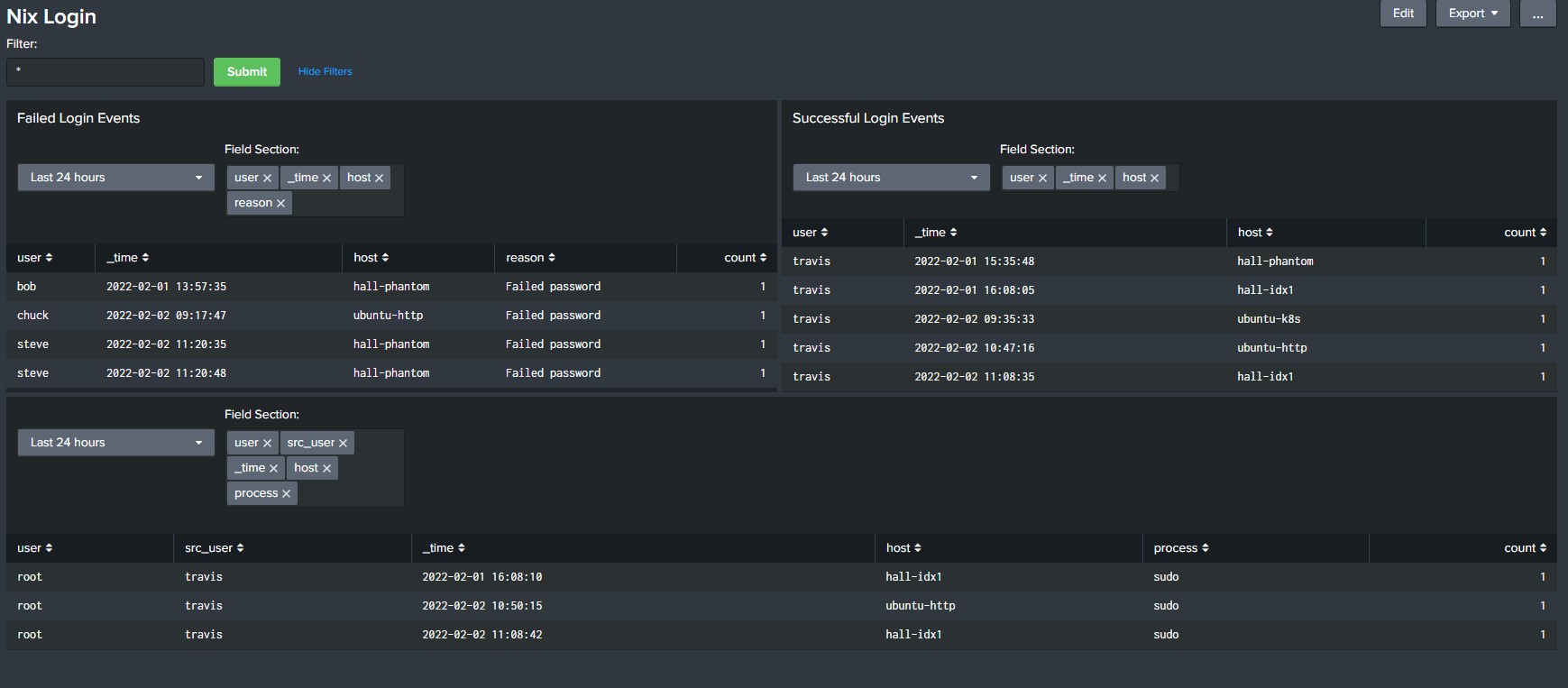
-
5 years, 4 months ago
thall wrote a new post
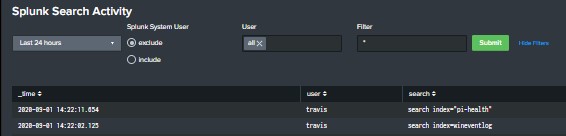
Built this dashboard to give a high level overview of user search activity. The search powering the dashboard is looking that the _audit index and you will need to ensure that you have proper access to the […]
-
6 years, 4 months ago
thall wrote a new post
In my previous role I created this dashboard to identify how much data a Splunk forwarder had sent to my indexers. This was a daily check that either myself of someone on my team would review. This check h […]
-
6 years, 5 months ago
thall wrote a new post
(updated on 8/26/2020)
Working with a customer I started this dashboard to give a high level overview of Windows Sysmon data. I have been evolving the dashboard in my home environment and will take any feedback […]
-
6 years, 7 months ago
thall wrote a new post
This search is still a work in progress, but thought I would go ahead and post it. Currently use OPNsense firewall in my house. The purpose of the search is to identify blocked scanning activity on my firewall t […]
-
6 years, 7 months ago
thall wrote a new post
Windows dashboard to help identify users that have either failed or successfully logged in. At the top you have a box I called “Filter” that allows you to insert search parameters in the base search (ex: […]
-
6 years, 8 months ago
thall commented on the post, Windows RDP sessions
In reply to: thall wrote a new post Windows RDP sessionsHere is a dashboard I built to look at Windows Logon Type 2 & 10 (remote & remote interactive) that will help identify which users access which servers and […] ViewAfternoon, the field input at the top of the dashboard is designed to be a generic filter and not tied to any specific field. If you want you can either enter a value or field=value and it should filter the dashboard accordingly. I pulled the dashboard in my home environment and everything works including the drilldown and the field input.…[Read more]
-
6 years, 9 months ago
thall wrote a new post
Windows RDP sessionsHere is a dashboard I built to look at Windows Logon Type 2 & 10 (remote & remote interactive) that will help identify which users access which servers and […]
-
6 years, 11 months ago
thall wrote a new post
Here is a dashboard I built to help you understand the activity of services and MSI installs within a Windows machine. This dashboard utilizes Post Processing so there is only 2 searches that are launched when […]
-
6 years, 11 months ago
thall wrote a new post
Here is a dashboard that I have built to look at Windows Account Management events. The dashboard utilizes a drill-down that will feed a multi-select which is using a dynamic search to give you fields that are […]
-
7 years, 1 month ago
thall wrote a new post
This search should help identify which forwarders are connected and give you more information on the forwarders.
index=”_internal” sourcetype=”splunkd” source=”*metrics.lo*” group=tcpin_connections […] -
8 years, 1 month ago
thall wrote a new post
This eval for password can be easily used for any field where a user can accidentally type in a password or even worse both username/password during login which generates a failed event. Below example is for […]
-
8 years, 1 month ago
thall changed their profile picture
-
8 years, 1 month ago
thall became a registered member
-
8 years, 1 month ago
thall became a registered member

The problem is that the User field input is not configured correctly. It does nothing actually. I’m working on fixing the input, test it and post the code here
Afternoon, the field input at the top of the dashboard is designed to be a generic filter and not tied to any specific field. If you want you can either enter a value or field=value and it should filter the dashboard accordingly. I pulled the dashboard in my home environment and everything works including the drilldown and the field input. Unless you a speaking of a different part of the dashboard.
travis
Keep getting WDM-(X) users when I use the Logon type 2. Anyone know of a way to actually identify this type of user?
Thanks for bringing this to my attention.
Why you are getting the error is because the “join” command is looking for search that is not there.
There seems to be an issue with the GoSplunk site where part of the 2nd query that is wrapped in square brackets [ ] is not showing up in the post. However, when editing the post the whole query is there. I tried many ways to re-format the post, but was unsuccessful.
Here is the complete 2nd query, just remember to update the 2 spots with index=(your_index):
index=wineventlog $field1$ EventCode=4624 Logon_Type=2 OR Logon_Type=10 earliest=-30d@d latest=-24h user=$user$ | fields _time | timechart count span=1h | eval hour = strftime(_time,”%H”) | stats sum(count) as 30day by hour | join type=outer hour [search index=wineventlog $field1$ EventCode=4624 Logon_Type=2 OR Logon_Type=10 earliest=-24h user=$user$ | fields _time | timechart count span=1h | eval hour = strftime(_time,"%H") | stats sum(count) as 24h by hour]
travis