-
2 years, 2 months ago
sedi wrote a new post
check expected splunk version with realitysimply query to compare an expected splunk version with reality. simply adjust “expected_version” to your expected […]
-
3 years, 4 months ago
sedi wrote a new post
index=_audit action=edit* info=granted operation!=list host= object=*
| transaction action user operation host maxspan=30s
| stats values(action) as action values(object) as modified_object by […] -
6 years, 5 months ago
sedi wrote a new post
Quickly identify high amounts of skipped searches in your cluster or standalone SH(s):
index = _internal skipped sourcetype=scheduler status=skipped host=[your splunk SH(s)]
| stats count by app search_type […] -
6 years, 5 months ago
sedi wrote a new post
Blocked queues are (obviously) bad for your environment so here a search to identify those:
index=_internal sourcetype=splunkd group=queue (name=parsingQueue OR name=indexqueue OR name=tcpin_queue OR […]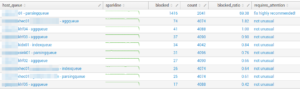
-
7 years ago
sedi wrote a new post
The following will:
list all knowledge objects for your SH (or given search peer(s))
each objects name, type, app, permissions, sharing (e.g. global, app, private) and owner
if props-extract:
the props […] -
7 years ago
sedi wrote a new post
Ok that one is a big one so be prepared ;)
The following will (on a SH / SH Cluster):
list all users and their roles
list inherited roles
list all indexes allowed by the shown roles
list all indexes […] -
7 years, 1 month ago
sedi wrote a new post
Total count of all events for 1 or more index(es)
Approach 1 (fastest)
| eventcount index=foo
or
| eventcount index=foo index=bar
does *not* support time ranges in the time picker
tested on: splunk […] -
7 years, 1 month ago
sedi became a registered member
-
7 years, 1 month ago
sedi became a registered member

This is awesome!